Top tips against phishing attacks
Be Cyber-Alert not Cyber-Alarmed
Cyber threat actors are trying to capitalize on the global health crisis by creating malwares or launching attacks with a COVID-19 theme.
With your teams working from home, it is more important than ever to remain vigilant.
Don’t click on links you might receive via text message or email, especially if the subject matter is focused around the coronavirus without caution.
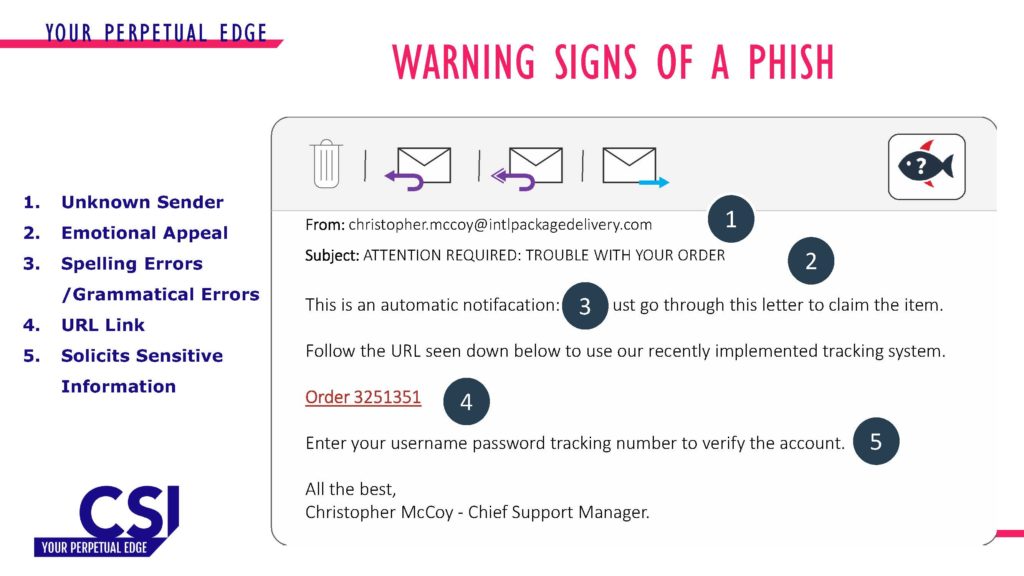
What is phishing and how does it work?
A phishing attack is a cyber-attack designed to gain unauthorised access to a network to wreak havoc on an individual or organisation.
It works by tricking a victim into opening a message and clicking on a malicious link. Usually, cyber criminals do this by pretending to be a trusted source, service, or person that a victim knows or is associated with.
To protect yourself from phishing, we recommend you:
- Don’t click on links in emails or messages, or open attachments, from people or organisations you don’t know.
- Look for spelling and grammatical errors and are hyper-aware of emails and texts containing emotional appeals soliciting sensitive or personal information.
- Hover over a link to see the web address before you click it. The actual web address is usually shown at the bottom of the browser window.
- Ask a family member or friend. One of the key defense mechanisms against phishing is a peer who sits alongside you, but with remote working that peer is no longer there. So, if you’re not sure, talk through the suspicious message with someone.
- Check legitimacy by contacting the relevant business using contact details sourced from the official company website.
Recommended security practices for businesses:
With more and more employees working from home, there are some key security practices that we recommend businesses consider.
1. Alert employees about the potential for phishing
Ensure staff know how to spot a phishing email. We can help you with sample Covid-19 phishing emails, so your teams have an idea of what to look out for.
2. Use multi-factor authentication
At home, workers may have to identify themselves to online work systems in a new way. Multi-factor authentication allows a business to be comfortable that the employee is who they say they are, regardless of the location they work from.
3. Decide on a chain of command
If your team is spread across the country, or even internationally, it’s important to decide how decisions get made in case of online disruption. Plan your cyber incident response processes. Whether you have 10 or 10,000 people, putting guidance in place on how to handle incidents will help you make good decisions under the pressure of a real incident.
CSI Managed Phishing Defence Service
CSI has recently partnered with Cofense to offer managed phishing defence service to our clients. https://cofense.com/
This also facilitates CSI in assessing the effectiveness and adoption of the advice internally by staff, as we conduct our own internal phishing campaigns and training.
CSI’s cyber defense team will continue to analyse our client environments and advise on any future developments where the COVID-19 pandemic is being used by threat actors.
Cofense has set up a Coronavirus Phishing Infocentre you can access here: https://cofense.com/solutions/topic/coronavirus-infocenter/
If you would like to find out more about how CSI can help you with your security requirements please call 0800 1088 301 or contact us.
Related articles:
National Cyber Security Centre guidance for home working https://www.ncsc.gov.uk/news/home-working-increases-in-response-to-covid-19
Bloomberg news https://www.bloomberg.com/news/articles/2020-03-16/u-s-health-agency-suffers-cyber-attack-during-covid-19-response
Security Affairs News https://securityaffairs.co/wordpress/99446/cyber-crime/coronavirus-map-delivers-malware.html
National Cyber Security Centre advice for cyber incident response processes https://www.ncsc.gov.uk/collection/incident-management/cyber-incident-response-processes
By Leyton Jefferies, Head of Cyber Security Services & Solutions
Ready to talk?
Get in touch today to discuss your IT challenges and goals. No matter what’s happening in your IT environment right now, discover how our experts can help your business discover its competitive edge.